Okta
Okta integration¶
Comet supports OAuth2 authentication from an approved Okta application. Once an Okta application has been integrated, a specific Comet URL can be used to login.
New users logging in for the first time will automatically have a new user created using Okta user information. Once logged in, the user can perform all actions a normal login provides.
Basic Requirements¶
Prerequisites Comet Implements an Okta Authorization Code Flow. The Okta Documentation to setup an Application can be found here.
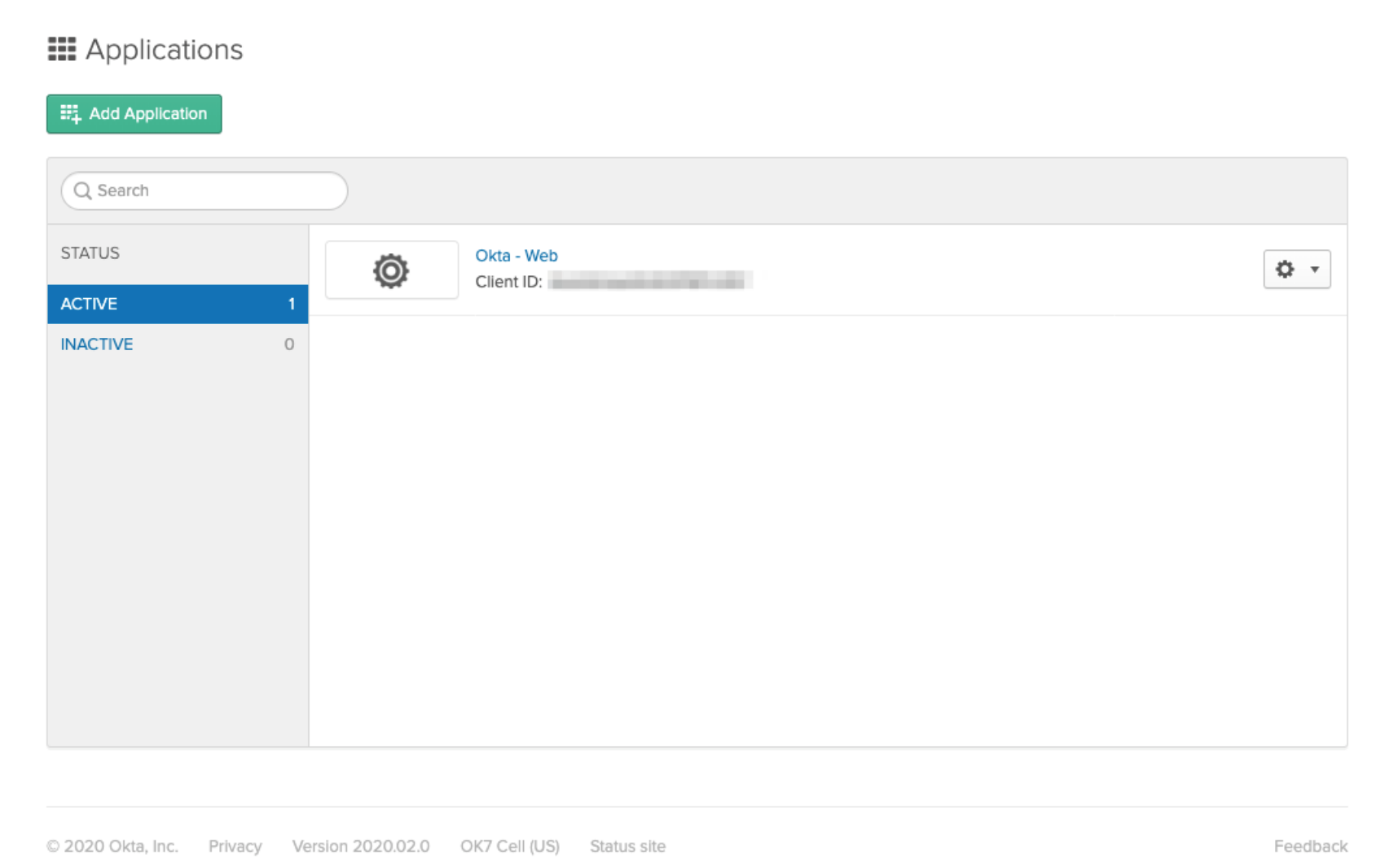
A sample application has been highlighted below.
Once the Okta Web Application is successfully created, go to the General tab
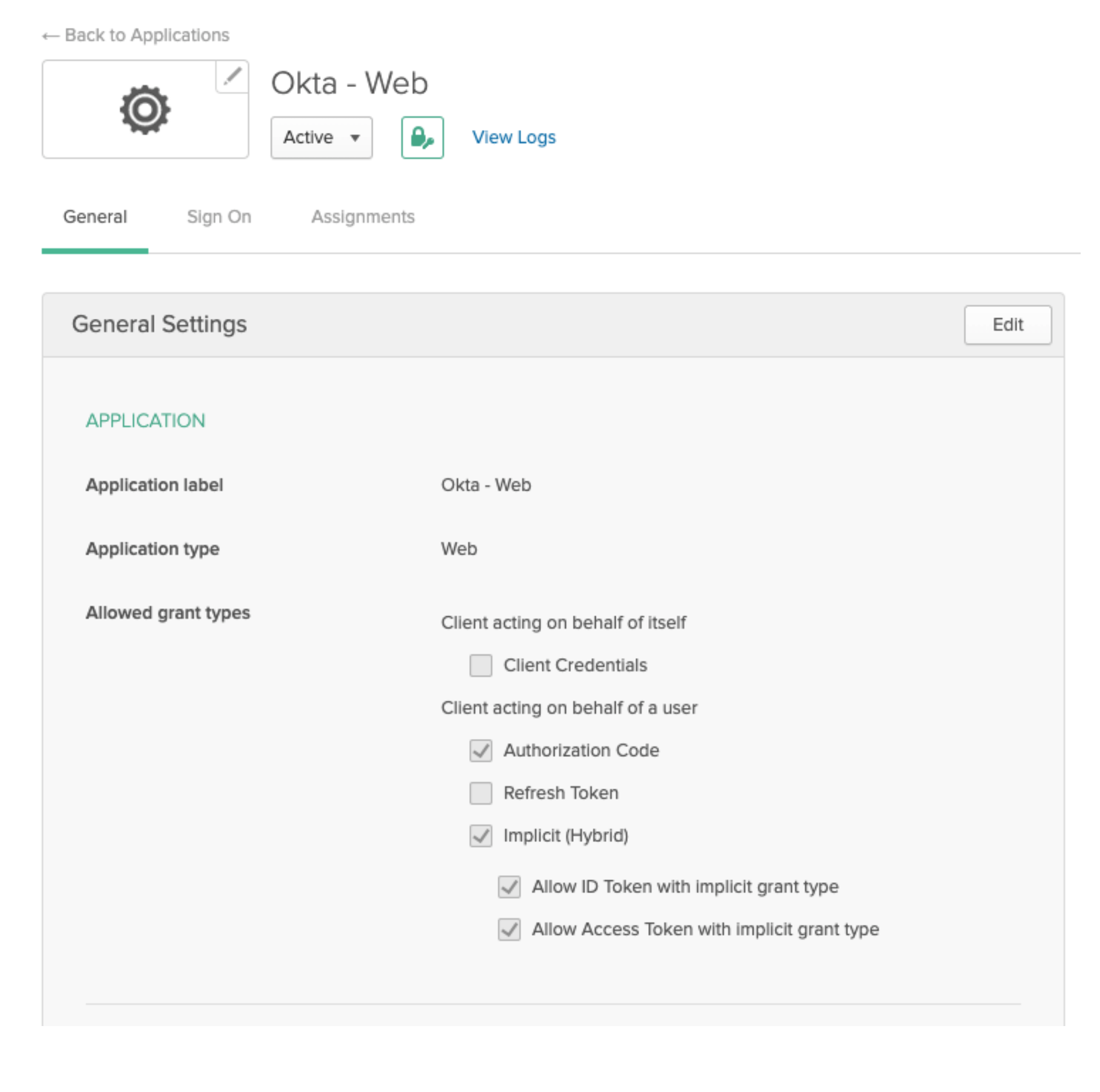
Application Settings¶
The web application should match the Grant Type settings below:
Sign on page:
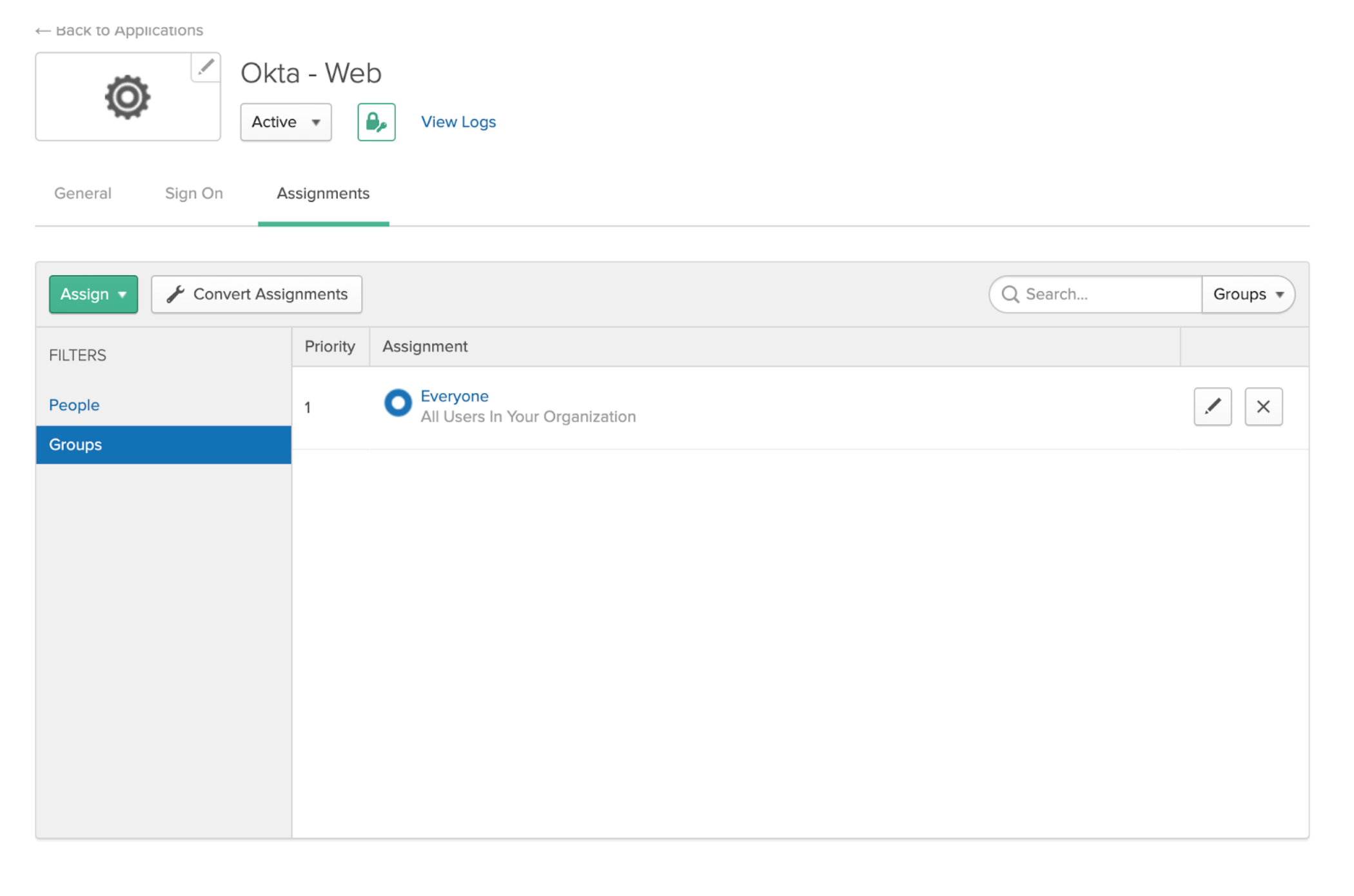
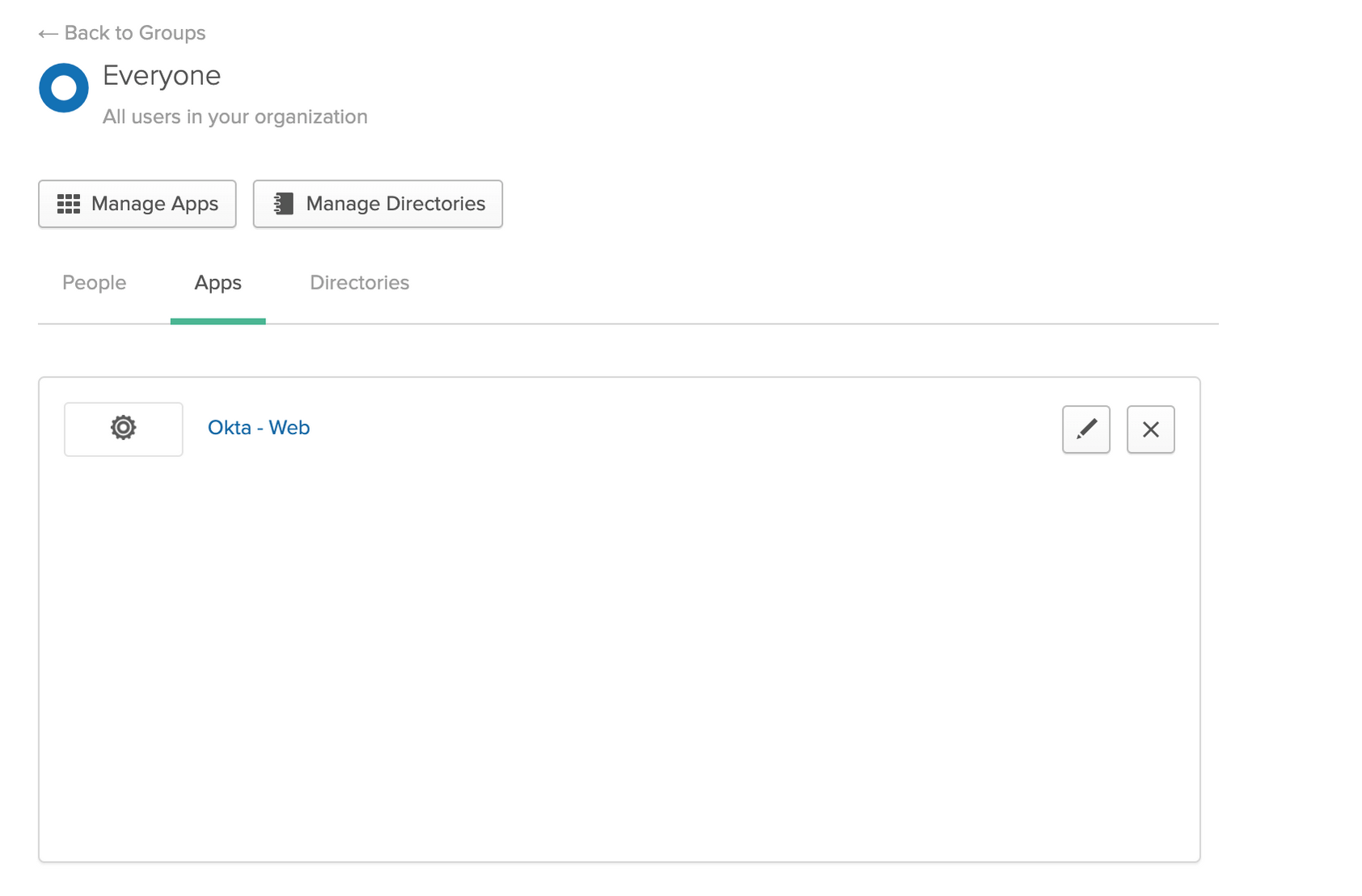
User Assignment¶
Select the group containing all users in your organization
Add the everyone group to the created Comet Okta application
If you would like to limit access you may also grant access to individual users or subsets of your organization using Okta groups.
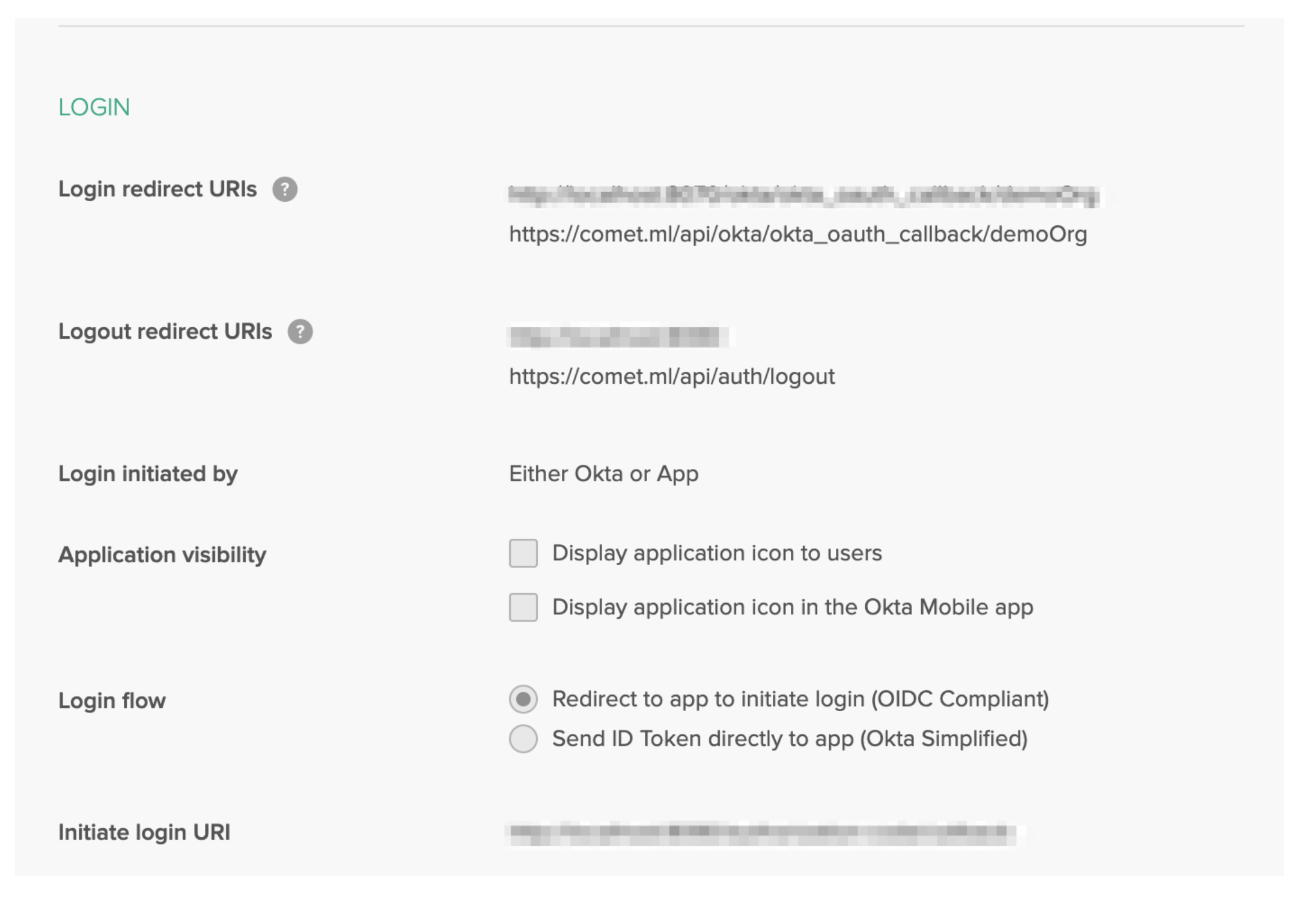
The login section contains URL’s that point to Comet.
- Login redirect URIs: https://comet_base_domain/api/okta/okta_oauth_callback/okta
- Logout redirect URIs: https://comet_base_domain/api/auth/logout
- Initiate login URI: http://comet_base_domain/okta-login
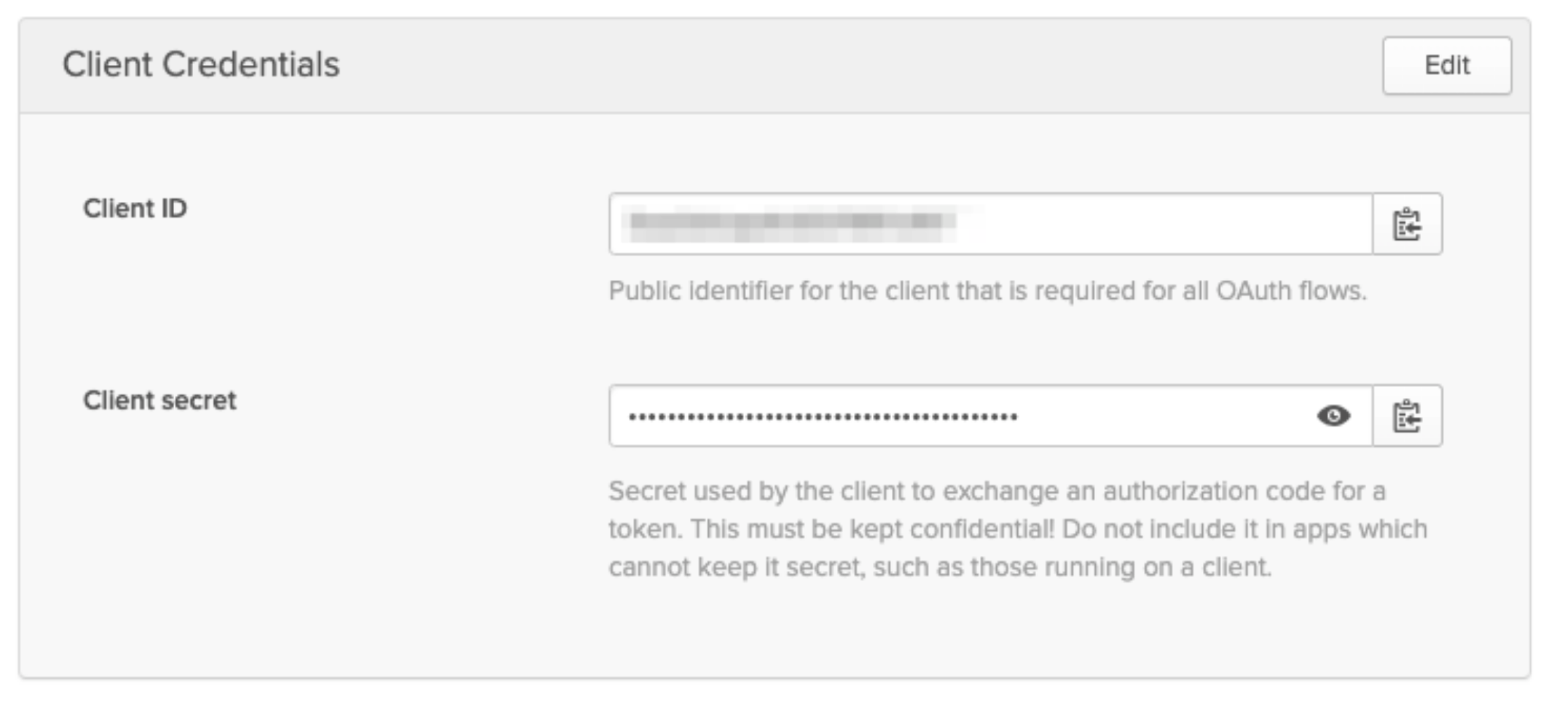
Client Credentials¶
The client credentials are required to retrieve user information and authenticate the user against Okta's directory.
Take note of the credentials as you'll be using these shortly.
Configuring Comet to use Okta on Linux installs¶
Run cometctl aio update-config and set/replace the following variables:
Replace the existing environment_token with the following value: environment_token: onprem-okta-auth
Append the following to the end of the file, replacing on_prem_okta_client_key and on_prem_okta_client secret with the credentials retrieved from the previous step.
okta_oauth_enabled: true
on_prem_okta_client_key: "123456w4nt0OFMYv357"
on_prem_okta_client_secret: "1234567-MW37609JLQjBbjpm9BnR6NPYL-YFLe8T3"
on_prem_okta_token_url: "https://your-app.okta.com/oauth2/default/v1/token/"
on_prem_okta_authorize_url: "https://your-app.okta.com/oauth2/default/v1/authorize"
on_prem_okta_user_info_url: "https://your-app.okta.com/oauth2/default/v1/userinfo"
If you're configuring this as part of your installation, you may now run cometctl aio install
Configuring Comet to use Okta on Kubernetes/Helm installs¶
Set the following variables in your local values.yaml.
frontend:
environmentToken: "onprem-okta-auth"
backend:
oktaOauthEnabled: true
oktaClientKey: "123456w4nt0OFMYv357"
oktaClientSecret: "1234567-MW37609JLQjBbjpm9BnR6NPYL-YFLe8T3"
oktaTokenUrl: "https://your-app.okta.com/oauth2/default/v1/token/"
oktaAuthorizeUrl: "https://your-app.okta.com/oauth2/default/v1/authorize"
oktaUserInfoUrl: "https://your-app.okta.com/oauth2/default/v1/userinfo"
helm upgrade --namespace default -f values.yaml comet-release comet-ml/cometml
Check if your changes has been applied¶
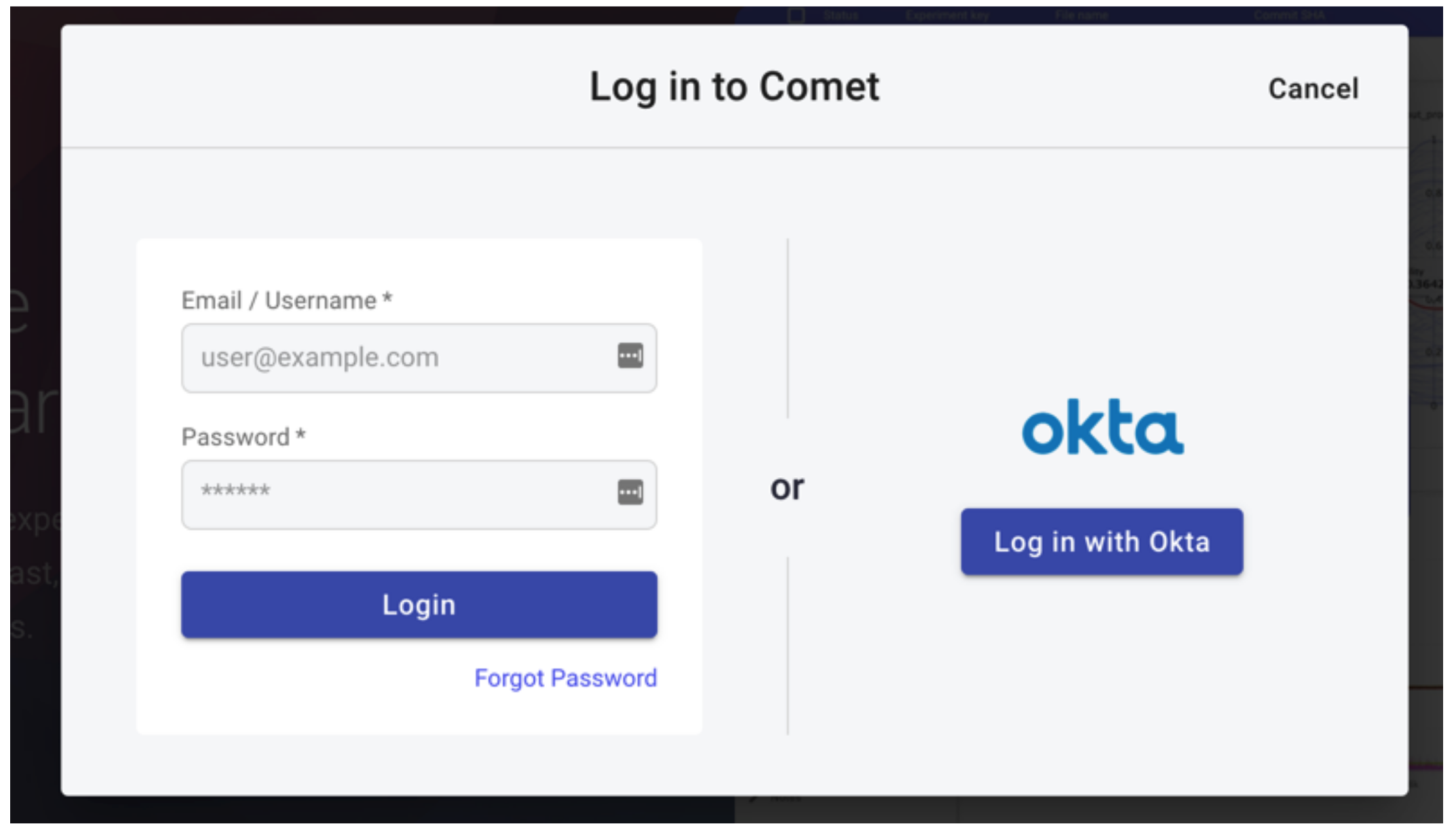
After this, navigate to your Comet domain:
And you should see an option to log in using Okta: